Simple Cloud Identity Management (SCIM) Protocol is a standard-based provisioning and de-provisioning user identity to the cloud-based SaaS applications. SCIM’s pragmatic approach it is designed quick and easy to move the user identity across the cloud applications. It’s mainly intent is to reduce the cost and complexity of user management operations by providing a common user schema and extension model, as well as binding documents to provide patterns for exchanging this schema using standard protocols.
SCIM is built on a model where a resource is the common denominator and all SCIM objects are derived from it. SCIM has three objects that directly derives from the Resource object. The ServiceProviderConfiguration and Schema are used to discover the service provider configuration. The Core Resource object specifies the endpoint resources User, Group and Organization.
The SCIM protocol exchange the user identities between two applications over HTTP protocol using REST (Representational State Transfer) protocol. SCIM protocol exposes a common user schema and resource object expressed JSON format and XML format. SCIM requests are made via HTTP requests with different HTTP methods and responses are returned in the body of the HTTP response, formatted as JSON or XML depending on the request.
Following are the SCIM Endpoint services for standard-based user identity provisioning and de-provisioning across cloud-based applications.
# SCIM provides two end point to discover supported features and specific attribute details.
• GET /ServiceProviderConfigs – This endpoint specify the service provider
specification and compliance, authentication schemes and data models.
• GET /Schemas – This endpoint specify the service provider’s resources and attribute extensions.
# SCIM Provides a REST API with simple set of HTTP/HTTPS (For CRUD) operations.
• POST – https://endpoint.com/{v}/{resource} – Create a new resource or Bulk resource.
• GET – https://endpoint.com/{v}/{resource}/{id} – Retrieves a particular resource.
• GET – https://endpoint.com/{v}/{resource}?filter={attribute}{op}{value}&
sortBy={attributeName}&sortOrder={ascending|descending} – Retrieves a resource with filter parameters.
• PUT – https://endpoint.com/{v}/{resource}/{id} – Modifies a resource with a
complete, consumer specified resource (Replace the full resource).
• PATCH – https://endpoint.com/{v}/{resource}/{id} – Modifies a resource with a set of
consumer specified changes (Update particular resource).
• DELETE – https://endpoint.com/{v}/{resource}/{id} – Deletes a resource. (Delete particular resource)
How SCIM protocol to provision the user identities into the Cloud (SaaS) application.
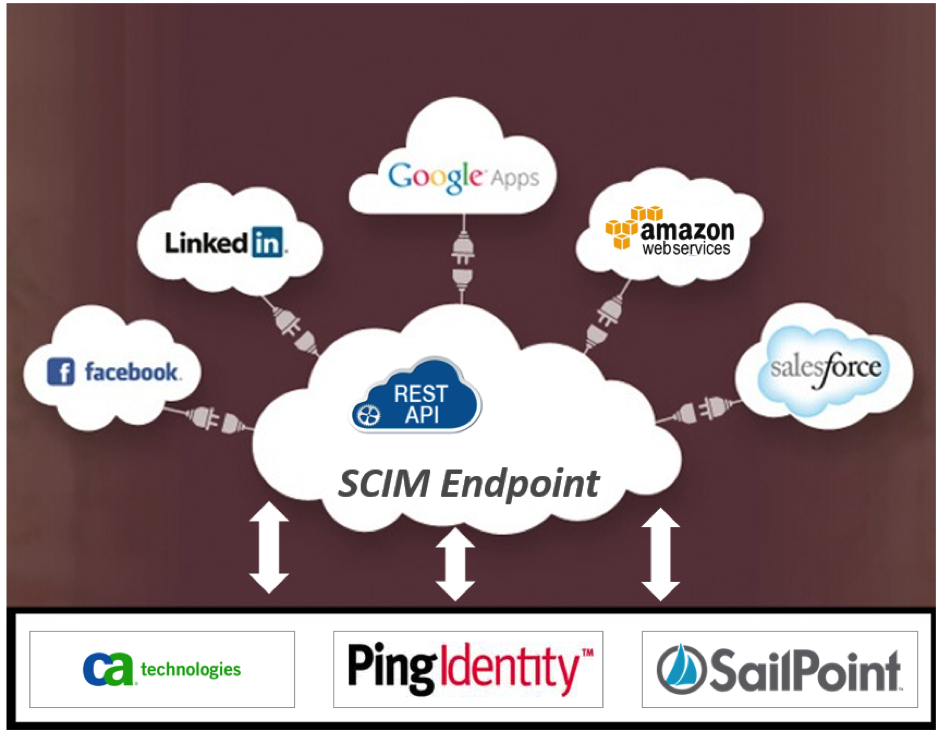

The SCIM protocol does not define a scheme for authentication and authorization therefore Service Provider are free to choose mechanisms appropriate to their use cases. Most of the SaaS applications (Service provider) provide OAuth2.0 security protocol for authentication and authorization, some of the SaaS application provide their own authentication mechanism. However now days most of the IDM vendors (CA, SailPoint, PingIdentity.) support SCIM protocol.
If you need more information about on this SCIM protocol refer this link http://www.simplecloud.info/





